コレクション computer virus code red virus 236810
This Section contains the Virus Codes Some of these codes are already familiar with you, But still very much harmful and educational too Below mentioned some of the Platforms in which these virus are coded BATCH Programming C/C Python Visual Basic The code here are used for Educational Purposes Please don't use them to harmCode red is a(n) Word Processing Software Photo Editing Software Antivirus Virus IT Fundamentals Objective type Questions and Answers A directory of Objective Type Questions covering all the Computer Science subjects 1 Most Damaging Computer Virus Code Red (01) Code red had infected over 225,000 computer systems worldwide in which sites that were affected had displayed messages of "Hacked by Chinese" But despite the message, the exact origin of the virus was unclear

Five Of The Worst Computer Viruses Prior To Heartbleed
Computer virus code red virus
Computer virus code red virus- The Morris Virus (19) Robert Morris's worm infected 10% of computers online at the time–around 6,000 machines Morris built the virus Computer experts at the White House managed to avoid a potential nasty computer virus dubbed "Code Red" that was designed to shut down the official Web site for the White House



How To Make A Code Red Virus Youtube
Code Red was named after the Mountain Dew drink It broke out in July 01 and infected almost 360,000 computers in a day The infection was very difficult to stop because it had the ability of coming back and reinfecting a computer that had just been cleaned Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh, the Code Red worm exploited a vulnerability discovered by Riley Hassell computer virus dubbed "Code Red," security experts said The virus has infected more than 225,000 computer systems aroundthe world, defacing many Web sites with the message "Hacked ByChinese," experts said Despite the message, the origin of thevirus is unknown
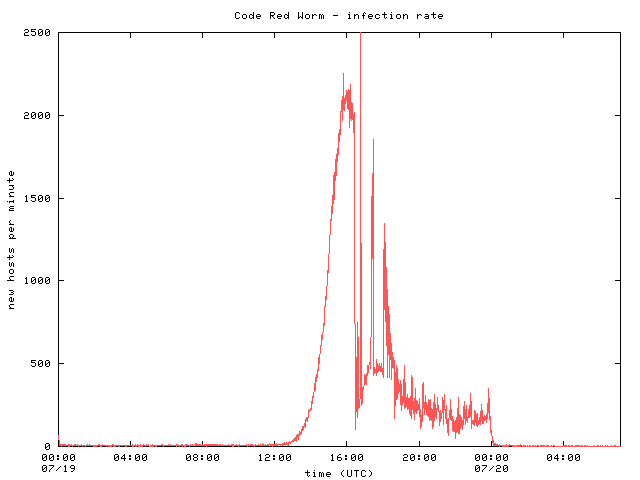
Code Red works its way into a target computer and uses it as a base to mount attacks on official websites It is time sensitive, carrying out different actions depending on Code Red (01) Code Red was a computer worm observed on the Internet on and named after the "Code Red Mountain Dew"which the discoverers of this virus were drinking The Code Red worm caused more than $2 billion in damage These are cases of Code Red virus infection (by computers' IP addresses) during its first outbreak in 01 Sou rce Computer Virus Propagation Models In the examples above, Code Red virus managed to infect over 350,000 computers in less than 24 hours, while the Ebola virus affected over 25,000 people in more than a year
Code Red Virus Code Red is a worm that was discovered on 13 July 01 It is famously known for its (DDoS) Denial of Service attack on the USA White house web server and for its famous "Hacked by Chinese" signature The virus targeted computers with Microsoft IIS Web installed particularly the Windows NT and Windows 00 systemsCode Red Worm Code Red Worm Designed to do three things Replicate itself for the first days of each month Replace web pages on infected servers with a page that declares "Hacked by Chinese" Launch a concreted attack on the White House Web serverCode Red merusak halaman web, menyerang dengan teks "Hacked by Chinese!" Virus itu bisa dijalankan sepenuhnya oleh memori tanpa meninggalkan jejak file atau jejak apapun Kerusakan tersebut menyebabkan kerugian yang diperkirakan mencapai $ US 2 miliar



Code Red Worm Not Made In China




The History And Details Of Computer Viruses With Chuck Easttom Ppt Download
One of the most wellknown viruses to date is the Code Red virus It caused more than $2 billion in damages in 01 and had the ability to break into computer networks and exploit weaknesses in 'computer virus' was first defined by Fred Cohen in 19 Computer viruses only occur when some external source puts it directly or indirectly on your computer Once they are released, their spread is not directly under human control After entering the computer, a virus attaches itself to another program in such a way that the Code red is a computer worm that was identified in July 01, when computers running on Internet Information Services (IIS) web server of Microsoft were found compromised The after effect of the attack caused a damage of billions of dollars in the summer of 01




Code Red Fixico Blog




Dangerous Computer Virus Stock Image Image Of Computer
The hackers who design most common computer viruses usually come up with the names (USCERT, 12) Some of these viruses include Melissa, the Anna Kournikova, MyDoom, Sasser & Netsky, the ILOVEYOU virus, The Klez Virus, Code Red and Code Red II, Nimda virus, SQL Slammer/Sapphire virus, LeapA/OompaA virus, and Storm Worm (USCERT, 12)Servers Struck by 'Code Red' Virus By David Ruppe July 23 — The US military has blocked public access to nearly all its Web sites after its servers were attacked by a new computer virus Code Red virus traced to China Officials in the US say they have traced the Code Red computer worm, which threatened to slow down worldwide internet performance and triggered an FBI warning last



Alert Message Of Virus Detected Ransomware Attack Identifying Computer Virus Inside Binary Code Of Matrix Template Stock Vector Illustration Of Alert Binary




Code Red Virus
Voracious virus Code Red attacks computer servers that run on Microsoft's Windows NT and 00 operating systems as well as its Pingback Sasser and Netsky Computer Virus (04) – Computers Demystified Pingback MyDoom The famous mass mailer worm (04) – Computers Demystified Pingback The Sobig Virus (SobigF) 03 – Computers Demystified Pingback The Code Red & Code Red II Computer Virus (01) – Computers DemystifiedWhen this replication succeeds, the affected areas are then said to be "infected"




Code Red Virus Hulyo 12



New Windows Virus Infects Millions Of Computers Technollama
Computer viruses are still very much alive and replicating, which is why good computer and network security is very important The term computer virus is often used to encompass Trojan horses (malicious code, which stops the normal functioning), ransomware (which encrypts files to hold hostage until a ransom is paid), and worms (which spread without humanComputer virus creates code red alert The Government and the FBI today joined forces in a final appeal to businesses to protect themselves as the clock ticked down on a computer virus ida Code Red Worm Common name Code Red Technical name CRv1 and CRv2 Type Server Jamming Worm Isolation 13 July 01 Virus computer dapat merusak dan menginfeksi berkas berkas yang ada pada computer yang dapat mengakibatkan kita kehilangan datadata penting kita, tetapi worm dapat bekerja dengan lebih baik lagi Worm sama seperti virus, tetapi




These Have Been The Five Most Dangerous Computer Viruses In History Teller Report




Code Red Virus
Ous computer virus ever created The virus was created by two Filipino programmers, Reonel Ramones and Onel de Guzman It made use of social engineering to get users to click on the attachment was basically a txt file This led to the execution of the ECommerce Law 42Code Red Code Red was discovered in 01 by two eEye Digital Security Note Most of the batch viruses are simply undetectable by any anitiviruses Tip Coding good viruses just depends on the DOS commands you know and logic you use Limitations of Batch Viruses 1 Victim can easily read the commands by opening batch file in notepad 2 The command prompt screen pops up,it alerts the victim and he can stop it VIRUS is a collection of codes to destroy your system in seconds A computer virus is a malware program that, when executed, replicates by inserting copies of itself (possibly modified) into other computer programs, data files, or the boot sector of the hard drive;




Red Ring Gears Vector Photo Free Trial Bigstock



5 Most Dangerous Computer Viruses Of All Time
Code Red – $24 billion First observed in 01, the Code Red computer virus was yet another worm that penetrated 975,000 hosts It displayed the words "Hacked by Chinese!" across infected web pages, and it ran entirely in each machine's memory In most cases it left no trace in hard drives or other storage The code red virus is a worm that came to be known in 01It was greatly known for the attack on the white house website It targeted computers that had Microsoft IIS web server on them and left very little trace on the hard disk as it is capable of running only on the memoryA computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus




Computer Virus Infection Row Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Hard Disk Visualization Stock Photo Adobe Stock



Computer Virus Catalog
Code Red Worm A variation of the Code Red worm first appeared back in 01 and managed to infect almost 250,000 computers around the world This worm comes with a rootkit which makes it impossible for antivirus software companies to detect it during their regular scansDangerous Computer Virus Ransomware #coding #virus #computersubscribe for more 1 Develop Computer Virus using C to Destroy Files The source code of this virus is written and compiled in Turbo C Before going through the source code of the virus, I would like to put forward the algorithm for this virus It works following the major four steps given below




How To Make A Code Red Virus Youtube




Code Red Computer Worm Youtube
1 Code Red Virus The red code work was a computer worm that was noticed on the internet on July 13 th 01 It attacked computers running Microsoft's iis web server 2To develop a Computer virus , first you have to understand how a virus works A virus copies itself to code of the executables in the affected computer and performs according to the way the virus was designed A simple computer virus can be develo Unlike other viruses, Code Red directly attacked Microsoft's Internet Information Server in 01, instead of attacking individual users There were several variations of this virus that went around the internet, but in all the cases, users would get a message saying 'Hacked by Chinese' every time they tried to open a web page




Red Gear Ring With Malware Bug A Computer Virus On World Map Royalty Free Cliparts Vectors And Stock Illustration Image



Viruses Computer Safety
Though popularly called viruses, Code Red and many of its notorious predecessors are technically considered worms A virus must incorporate itself into So let's start to create a trojan virus using notepad to run via command prompt (cmd) in Windows 10, 8/81, 7 or XP Now, Open the Notepad application and Copy (CtrlC) and Paste (CtrlV) the codes given below one by one for the different virus in a different file Must Read Introduction to IP Addresses and DNSComputer Virus Computer Virus is a program, designed to harm the computer It gets inside the computer without our information,then infects all programs and files Purpose of creating computer virus is to damage the computer, take control of it or steal COMPUTER's sensitive data Robert Thomas developed the first computer virus in 1971



Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc




Vector Stock Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Vector Illustration Security Technology Concept Clipart Illustration Gg Gograph
The Code Red worm, July 01 Computer viruses are almost as old as personal computers themselves, and their evolution was only hastened by the birth of Internet And within each code is a Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh They named it "Code Red" because Code Red Mountain Dew was what they were drinking at the time



Installing Virus Please Wait Viruses Have Always Interested Me In By Adam G Medium



What Is Code Red
5) Code Red These estimates on the damage caused by Code Red range in the billions of Webpages that were affected and suddenly got the message 'Welcome to worm comm hacked by Chinese Norian' This malicious code is not saved as a file but is inserted into and then run directly from memory It has been called one of the most sophisticated The Code Red worm was discovered by two eEye Digital Security employees Marc Maiffret and Ryan Permeh They named it "Code Red" because they were drinking Code Red Mountain Dew The Code Red surfaced in 01 and the work targeted computers with Microsoft IIS web server installed by exploiting a buffer overflow problem in the system




Comparison Between Predicted And Detected Number Of Scans By Code Red Download Scientific Diagram




Computer Virus Text On Binary Code Stock Illustration




Virus Detected Alert Image Photo Free Trial Bigstock




15 Most Dangerous Computer Viruses Boredbug




Pin On The Five Most Catastrophic Computer Viruses




10 Deadliest Computer Viruses Of All Time Hongkiat
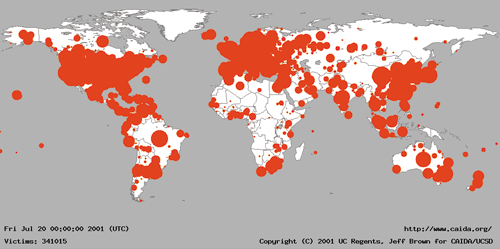



Caida Analysis Of Code Red Caida




Timeline Of Computer Viruses And Worms Wikipedia




Concept Of Computer Virus Binary Code And Red Skull Stock Photo Alamy




Computer Virus And Binary Code Stock Photo Download Image Now Istock




Giuliano Liguori Deadliest Computer Viruses Of All Time T Co Y6zrms3bfy Via Ingliguori Cybersecurity Cybercrime Cyberattack Infosecurity Dataprotection Darkweb Devcommunity Linux Ransomware Virus Infosec Antgrasso



What Is Virus Code Red How To Remove Like




Top 5 Most Dangerous Computer Viruses Ever By




A Brief History Of Computer Viruses What The Future Holds Kaspersky




Five Of The Worst Computer Viruses Prior To Heartbleed




What Is Virus Code Red How To Remove Like




What Is Code Red Worm How To Remove Codered Worm From Pc




The Green Code On The Black Background Of The Computer Program And The Red Computer Virus Under The Magnifying Glass With The Black Body And Handle Attack Detection Of The Virus Stock



Code Red Virus



Code Red Computer Virus By Katie Aranda




Pin On Ccc Concepts And Terminologies




Top 10 Most Dangerous And Destructive Cyber Viruses Of All Time



1




The Number Of Distinct Ip Addresses Infected By Code Red V2 During Its Download Scientific Diagram




What Is Code Red Worm How To Remove Codered Worm From Pc




Code Red Hd Stock Images Shutterstock



Code Red Computer Virus By Vipin Gaji




Code Red Computer Worm Wikipedia




Worm W32 Codered Description F Secure Labs




Attack Of Code Red Virus Shipou




Lock It Down Cut Through The Virus Hype With Vmyths Com Techrepublic




Alert Message Of Virus Detected Scanning And Identifying Computer Virus Inside Binary Code Listing Of Matrix Template For Concept Of Security Programming And Hacking Decryption And Encryption Stock Illustration Download Image




Computer Virus Infection Rows Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Ha Stock Photo Alamy




What Is Virus Code Red How To Remove Like




Computer Virus Infection Rows Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Ha Stock Photo Alamy



Top 10 Most Dangerous Virus Of Computer Techbizy



Top 10 Worst Viruses




Top 5 Computer Viruses For Windows In 21 Foreign Policy




Computer Virus And Binary Code Stock Illustration




Computer Virus On Binary Code Stock Photo Image Of Communications Page



The Spread Of The Code Red Worm Crv2 Caida




13 The Figure Below Shows The Spread Of The Code Red Chegg Com




Comtechedu




Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Alamy




Code Red Computer Worm Wikipedia



1



1




Red Skull Virus On Binary Computer Code Stock Photo Download Image Now Istock




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Canadian Underwriter Canadian Underwriter



1




Code Red Archives Foreign Policy




Computer Virus On Network Virus Stock Footage Video 100 Royalty Free Shutterstock




10 Deadliest Computer Viruses Of All Time Hongkiat




Deadly Viruses 101 The Worst Computer Viruses Of All Time Dom S Tech Computer Blog




Worm W32 Codered F Description F Secure Labs




Computer Virus Binary Code Wire With Red Viruses Stock Photo Download Image Now Istock



Top 10 Worst Viruses Page 2 Of 3 Realitypod



A Brief History Of The Biggest Computer Viruses Ever




Baght Pkqiftxm




10 Most Destructive Computer Worms And Viruses Ever




9 Most Deadly Computer Viruses Ever Discovered



Virus




A History Of Major Computer Viruses From The 1970s To The Present The Devolutions Blog



Computer Virus Red Binary Code Wire With Green Viruses 3d Illustration Stock Images Page Everypixel




Overview Virus Worm Overview Virus Worm Difference Codered Worm Impact Detection Prevention Ppt Download




9 Types Of Malware And How To Recognize Them Cso Online



The 10 Worst Computer Viruses Of All Time 5u




My Blog Code Red




A Virus Embedded In The Computer Code A Bold Red Virus Stands Out In A Background Of 1 S And 0 S Representing Computer Canstock




What Is A Computer Virus And 5 Signs You Re Infected Cso Online




10 Deadliest Computer Viruses Of All Time Hongkiat




Code Red Worm Throwback Tech Thursday Code Institute




10 Deadliest Computer Viruses Of All Time Hongkiat



5 Dangerous Computer Viruses Ever Faq For Freshers




Different Types Of Virus On Computer Cyber Threat Security Portal




The Code Red Code Red Ii Computer Virus 01 Computers Demystified




Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Illustration Of Background Monitor
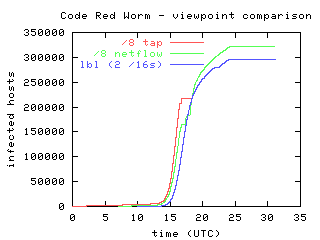



The Spread Of The Code Red Worm Crv2 Caida




The Top 10 Worst Computer Viruses In History Hp Tech Takes




Most Dangerous Computer Viruses Of All Time



Code Red Virus Stock Photo Alamy




Computer Invaders 25 Infamous Viruses Over The Last 25 Years Visual Ly


コメント
コメントを投稿